What Are the Financial Costs of a Data Breach?
The average cost of a data breach is $3.86 million, which is a conservative number, according to the Ponemon Institute. Some breaches go unreported because companies don’t want to damage their reputation or lose client trust.
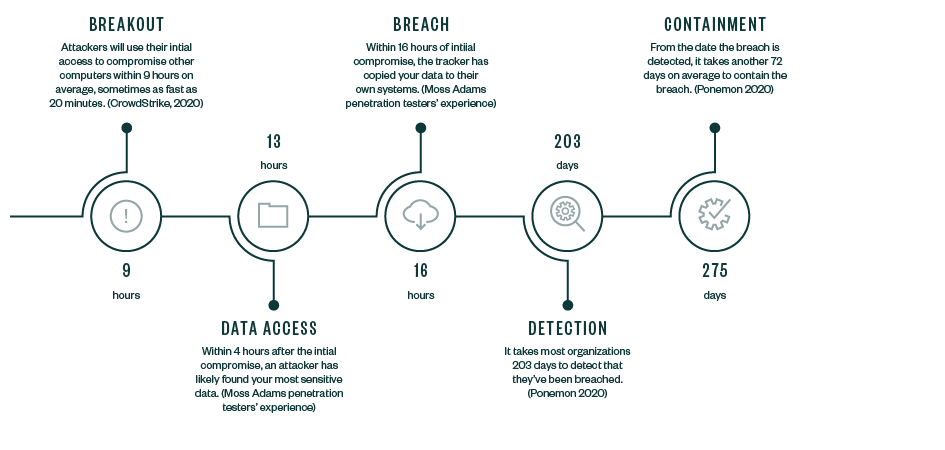
The average life cycle of a breach is 280 days, from identification to containment. During that time, there are costs an organization needs to account for.
Costs of a Data Breach
Associated costs of a breach can include:
- Paying off hackers
- Replacing hardware and software
- Decreased revenue from lost clients
- Increased costs of employees brought in to mitigate the damage
The timeline below demonstrates not only the immediate impact of a data breach, but also its far-reaching consequences and ways it could continue to affect your organization over much longer periods than you initially anticipate.
Lifecycle of a Data Breach
What Are the Intangible Costs of a Data Breach?
There are six main intangible costs to a data breach:
- Reputational loss
- Operational impairments
- Bank loan covenants
- Vendor liability
- Insurance premiums
- Buyers and investors
How Is Reputation Loss Affected by a Data Breach?
For all companies dealing with personal data, a public breach means an immediate loss of reputation and client confidence.
While large brands who are household names often get a lot of attention from the public and media, smaller companies can also face the same negative consequences when they expose client information to attackers.
Customers may feel violated and opt to do business with a competitor instead. They may also share their negative experience with your company with their network, posting about your breach on social media and leaving reviews of your company on public channels.
Lost clients aren’t the only risk. An episode of the IT Pro Podcast explored the ramifications of the 2014 Sony Pictures hack, which revealed information on actor compensation as well as some damning internal emails that led to loss of jobs and damaged public reputations of individuals at the company.
How Does a Data Breach Impair Business Operations?
While cyberattacks are costly to both the revenue and reputation of an organization, it can also impact businesses as usual, preventing or hindering core operations.
Some notable examples of ransomware disrupting businesses, including the JBS and Colonial Pipeline attacks, took days or weeks to resume operations back to the normal level.
JBS Attack
In June 2021, JBS, the world’s largest beef supplier and meat processing company, was a victim of a Russian cyberattack. The attack caused operations in 13 of JBS’s processing plants across three countries to stand still.
The company reportedly paid $11 million in Bitcoin to the attackers once back online to prevent a future attack and protect customer well-being.
Colonial Pipeline Attack
In May 2021, Colonia Pipeline, the largest supplier of gas on the eastern coast of the United States, discovered malware on its systems.
On May 7, pipeline operations halted, impacting customers who had to wait hours to fill-up their tanks, if they were able to find gas at all. The disruption lasted until May 17, when full operations were restored.
The breach cost the company $4.4 million in Bitcoin. Company leadership resorted to hiring a consultant to negotiate with the attackers.
How Does a Data Breach Affect Bank Loan Covenants?
In the past, banks would ask businesses for a copy of the balance sheet, financials, and quarterly projections.
In an increasingly digital and virtual world, financial institutions are considering plans to incorporate requirements to obtain an organization’s cyberattack plans and any investment in cyberattack insurance.
Banks and other depository institutions will evaluate their customer base. Based on risk assessment—the nature and volume of customer data held by a business, for example—the institution will assess the level of requirement as to any cybersecurity-related covenants. The requirements will largely depend on the nature of the borrower’s business.
Commercial business loans obtained from businesses that deal with large amounts of customer data will generally be the focus of a financial institution’s requirement for cyberattack plans and proof of cyberattack insurance. While cyberattack insurance isn’t mandatory, that does seem to be the direction banks are headed.
Consider the following example. You’re a small business that’s hit by a breach. You ask the bank to loan you money to mitigate the costs. It doesn’t impact the bank, but it does impact you.
How Does a Data Breach Affect Vendor Liability?
With so many organizations relying on third-party service providers to handle employee and customer data, it’s important to be aware of your liabilities as an organization.
Vendors are increasingly limiting their liability during contract negotiations, which leaves your company responsible if a breach with your vendor releases medical data, payment details, or other personally identifiable information of your employees and customers.
Some new laws, such as the California Consumer Privacy Act passed in 2020, make it possible for victims to file lawsuits for damages. In most cases, however, the entity responsible for controlling the data is primarily the one liable.
How Does a Data Breach Affect Insurance Premiums?
Companies are subject to greater underwriting scrutiny and ultimately increased premiums as attackers become more innovative and their attacks more sophisticated. This trend is anticipated to continue.
When it comes to cyber liability insurance, it’s important to understand the connection between controls, insurance companies, and underwriters when determining cost—and how solid cybersecurity policies could bolster your banking relationships, which can potentially lower your cyber liability premium.
A US Government Accountability Office (GAO) report on Cyber Insurance: Insurers and Policyholders Face Challenges in an Evolving Market revealed that more frequent and severe cyberattacks resulted in increased demand for cybersecurity coverage and higher insurer costs. In a survey of insurance brokers, more than half of respondents’ clients saw prices go up 10%–30% in late 2020.
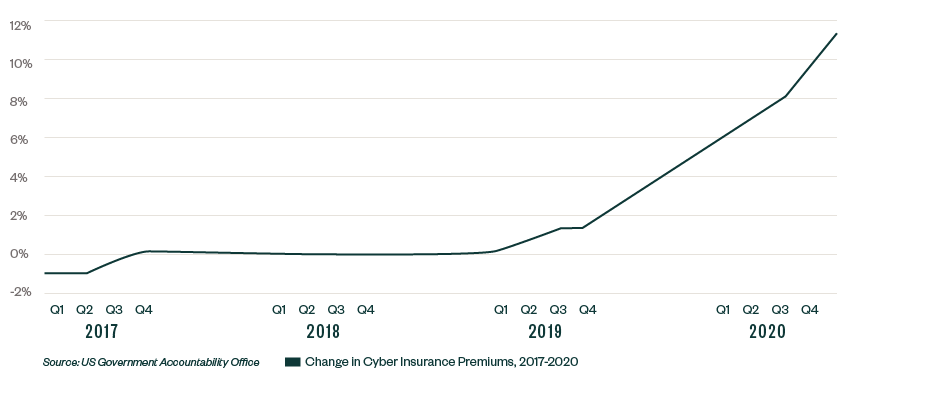
Insurance companies re-evaluate each year, and it can cost you more on premiums if you don’t take care of your business properly.
How Does a Data Breach Influence Buyers and Investors?
Buyers wants to make sure the companies they buy have good data hygiene; they don’t want to buy a company and find that they’re responsible for costs and lawsuits due to bad practices. Cybersecurity due diligence is imperative—and it should happen before transactions talks begin.
While not necessarily related to cybersecurity, scalability is important to buyers and investors. They want to make sure the technology in place is scalable and can grow as the company does without causing major infrastructure issues.
Different industries have different standards and assessments for evaluating the security of a company and its data. There are assessments that are pass/fail as it relates to the industry, the standards and requirements they need to meet, and how well they comply.
The Upward Trend of Cyberattacks
Attacking organizations is lucrative, which encourages attacks to continue.
Some of these attackers reside in other countries where they’re safe from prosecution for their crimes, making the risk low and the reward high. Once they obtain data, it’s sold on the black market with the attackers’ identify hidden.
Additional opportunities arose during the COVID-19 pandemic with a large percentage of the workforce shifting to remote work setups. Remote work IT systems and unsecured networks made employees more vulnerable with more entry points for attackers, who are becoming more sophisticated as they test and try to break into different systems.
As a result of 5G increasing the bandwidth of connected devices, Internet of things (IoT) devices will also become more vulnerable to cyberattacks.
Vulnerable Industries
Each industry has certain information that makes them attractive to cybercriminals. Here are some examples:
- Health care. These organizations are a wealth of personally identifiable information.
- Retail. Point of sale is at risk of being infiltrated and customer card information stolen.
- Manufacturing. This industry is known for trade secrets that can be exploited and sold.
While all industries need to be cautious, recent trends indicate that the rise of more sensitive and personal data in the cloud means cloud security something to be prioritized by any modern company.
Here are some of the groups and industries that are most vulnerable to cyberattacks:
- Small businesses
- Health care institutions
- Government agencies
- Energy companies
- Higher education facilities
10 Actions to Combat Cyberthreats and Build Confidence in Your Business
The following steps can help protect your business:
- Take inventory of all your information assets and perform a risk assessment.
- Perform systems hardening, this process could include changing default usernames and using stronger passwords on your network and any key information assets.
- Update device definitions and patches on a frequent basis for all key information assets, such as anti-virus protection, firewalls, system software updates, and mobile device management (MDM).
- Make wise technology choices by adopting the technology and safeguards that match your business model and risk appetite.
- Develop a robust third-party and vendor management review program.
- Conduct frequent application, network, web application, and application programming interface (API) security assessments.
- Conduct frequent security- and social-engineering awareness training.
- Maintain appropriate cybersecurity insurance.
- Implement real-time monitoring services such as firewall information networks.
- Have consistent and clear communication with every level of your organization with C-suite executives and upper-level management communicating frequently about the importance of cybersecurity.
We’re Here to Help
If you have questions about how a data breach could impact your insurance premiums and affect the relationship with your banking institution, please contact your Moss Adams professional.


